On July 2nd 2020, I found an Open Redirect on Facebook. The payload was not persistent, sometimes it worked, or you get a warning about visiting a malicious website (more details on this later). I submitted the bug to the Facebook Security Team right away, and have my fingers crossed for a good response for my report.
The Vulnerable URL (u= is the parameter in my control):
https://l.facebook.com/l.php?u=http%3A%2F%2Fwww.evil.com
%2F%3Ffbclid%3DIwAR3Jo2LHVsAK8gAy2OruoscIYQRmfsKpWZr3pnaSb9htZV9rvaBBHRX4rLI&h=AT0svEn448wRmHj0UL4xDFsmollRDU9540KJVdZ_-Abc3BJRL9x8OKhYij2K09HCrn8Na5IpPvgtCiVFyB69Mh-UTkczsovgGlRbIE0rR69d7x4IoPd4maM8Y5tB1NUBAGKTrMoPjRk
The next day, July 3rd, Facebook team replied:
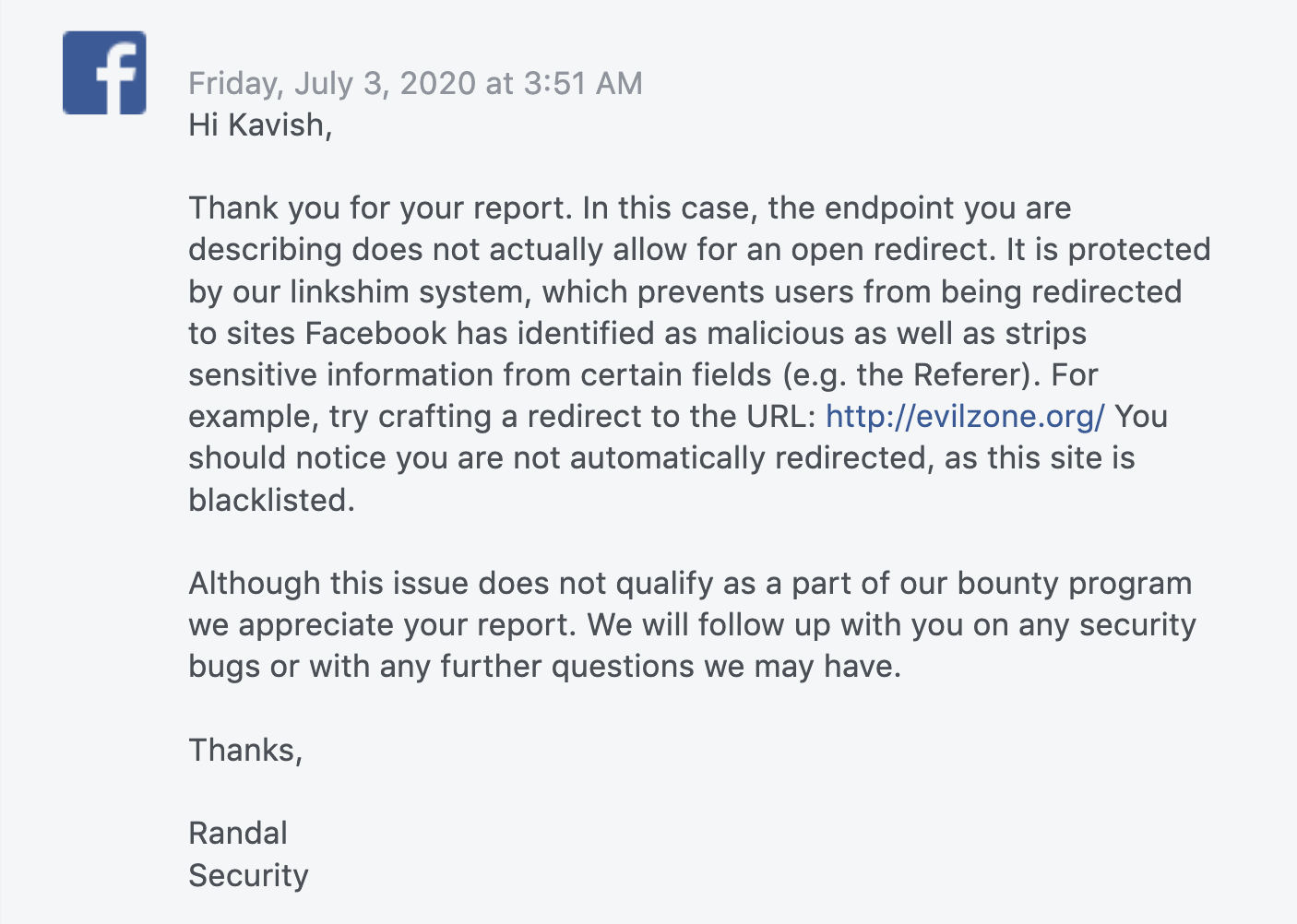
I was not dissapointed. You should never expect anything for a bug report. That way you won’t get disappointed and fall back in a performance pressure mood. Facebook doesn’t accept Open Redirect as a valid bug anyway.
Like I said, the redirect was not persistent. Which means that link shim sometimes let the request go through. I don’t why this keeps happening. It’s definitely not some sort of database that keeps track of malicious websites. Because once link shim came across a dangerous link, the next time you try to a redirect on the same malicious link, it should be blocked right away. Well, that was the part that scratched my mind, and is started doing some research.
Research On Linkshim
In 2012, Facebook Integrity Team wrote a tool called “link shim” to warn users about malicious links. It’s a very smart tool that makes use of analytics but there’s a catch.
The endpoint l.facebook.com/l.php takes 2 parameters:
- the url:
u=http://www.example.com - a hash:
h=AT0svEn448wRmHj0UL4....[TRUNCATED]
Upon each request, a user-specific hash is being generated. That particular hash is used to identify the user and is only valid for that user. The facebook server is basically making use of cookies to determine who that user is. Without the hash the request won’t go through.
Exploitation
Without cookies, the linkshim system can’t determined who crafted the link. Hence all domains are permitted. Scary right.
I fired up an incognito tab in Chrome, and open redirect was successful:
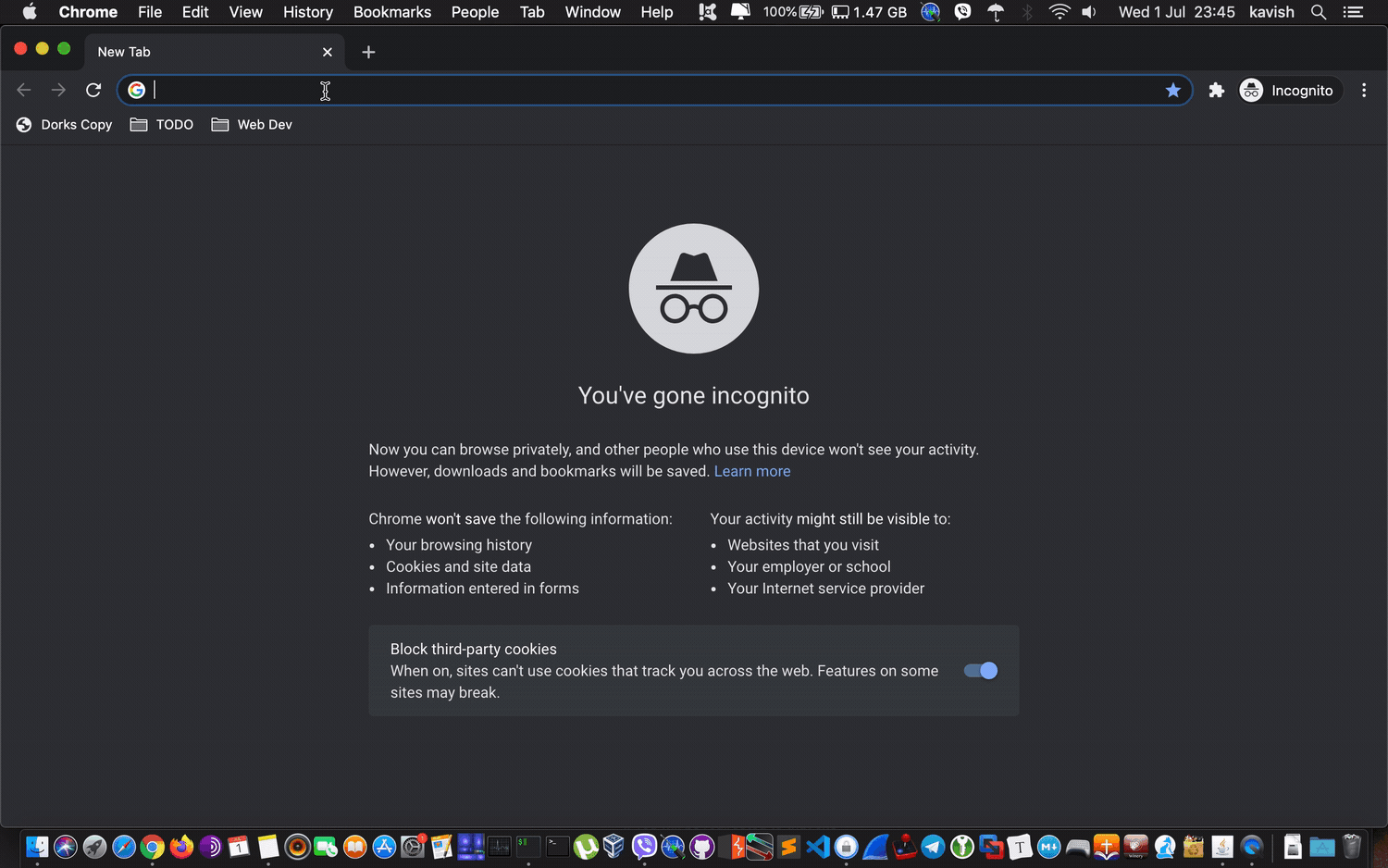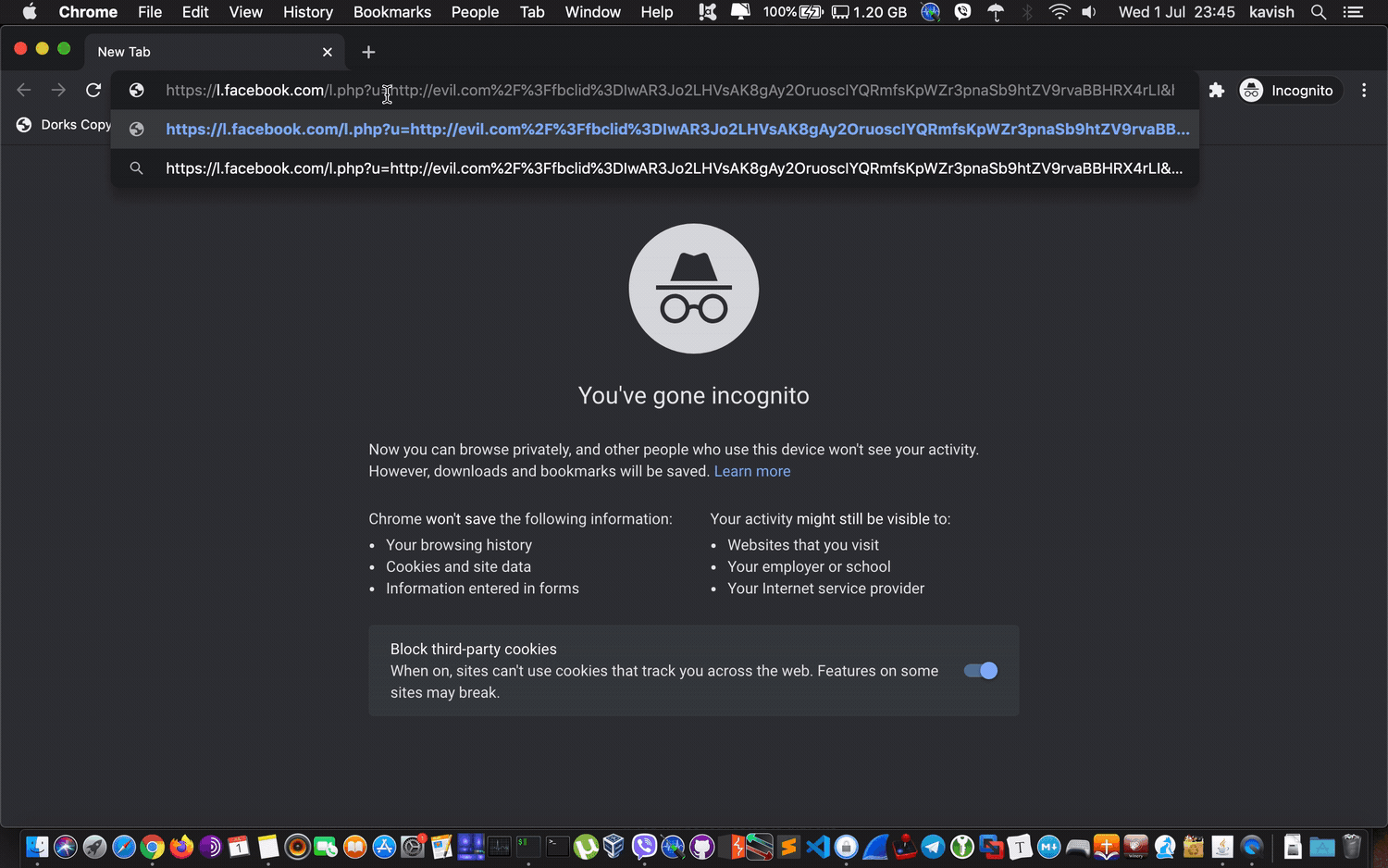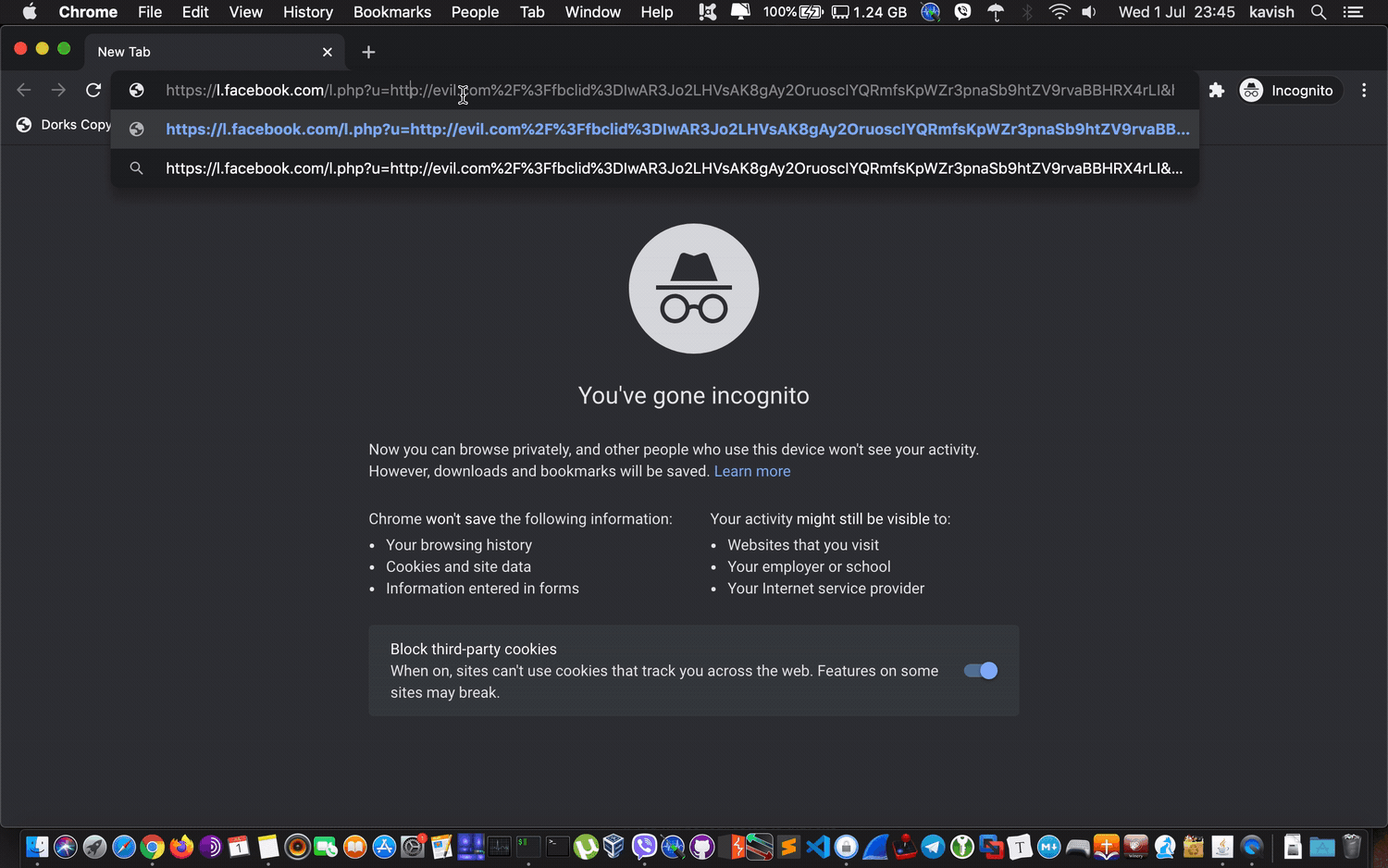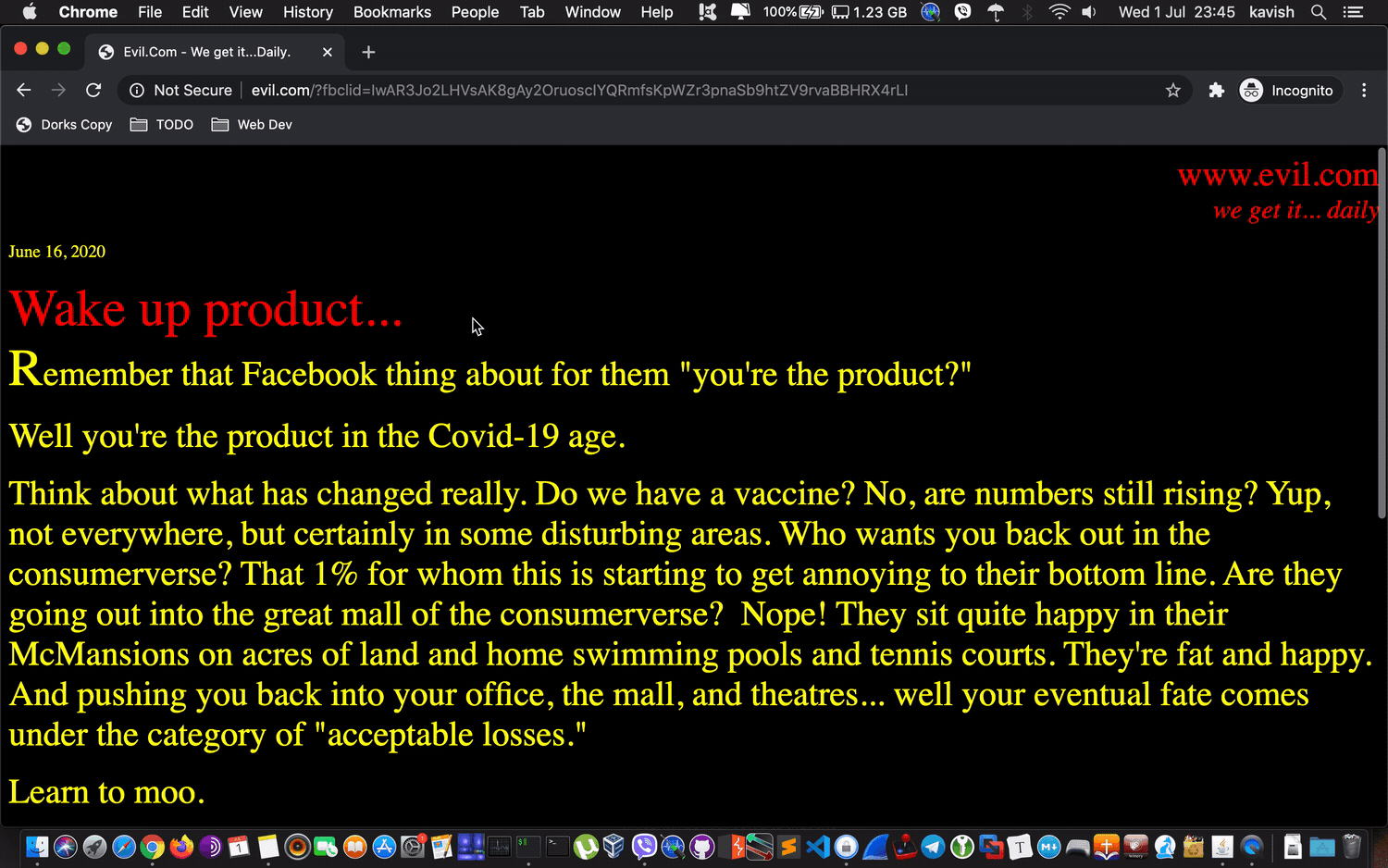
And now it’s fixed:
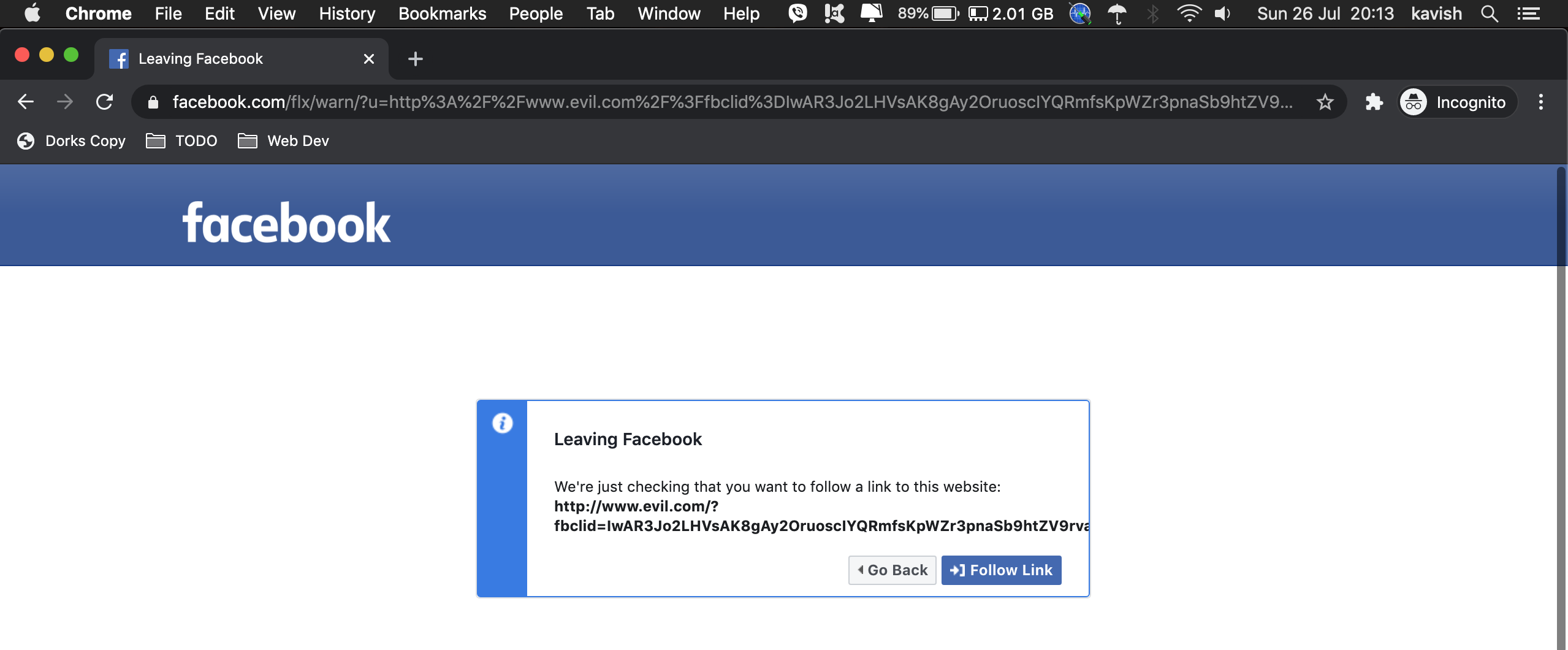
Impact
An attacker can take advantage of this URL for phishing attacks(create a fake login page to harvesting credentials). Additionally, URL encoding techniques can be used to hide the payload.
Reward
Even though they fixed it, Open Redirect is not eligible for a reward. Happy Bug Hunting.